Network and system security pdf Lower Macdonald

Network and System Security khalil shreateh security in distributed and networking systems Ing systems, and network interconnects must all be coher. Sdsc.edupublicationsteracrack.pdf.LEAP: Efficient Security Mechanisms for Large-Scale. George Mason.main components in data security management of distributed systems. Curity and network management problems until there
About IEC 62443-3-32013 Industrial communication
Computer security Wikipedia. protecting a local system or network of systems from network-based security threats while affording access to the outside world via wide area networks and the Internet Traditionally, a firewall is a dedicated computer that interfaces with computers outside a network and has special security …, for increase and strong computer and network security also becomes increasinly necessary and important. The increase in the computer network system has exposed many networks to various kinds of internet threats and with this exposure, one can see that the need for increased network security is vital and important in every organization. The.
system and network security terms, nor is it a compendium of every acronym and abbreviation found in system and network security documents published by NIST. Readers should refer to each document’s list of acronyms and abbreviations (typically found in an appendix) for … 05/05/2017 · Network and System Security provides focused coverage of network and system security technologies. It explores practical solutions to a wide range of network and systems security issues. Chapters are authored by leading experts in the field and address the immediate and long-term challenges in the authors’ respective areas of expertise.
La directive Network and Information System Security (NIS) vise à l’émergence d’une Europe forte et de confiance, qui s’appuie sur les capacités nationales des Etats membres en matière de cybersécurité, la mise en place d’une coopération efficace et la protection des activités économiques et sociétales critiques de la nation, pour faire face collectivement aux risques de This book constitutes the refereed proceedings of the Third International Conference on Future Network Systems and Security, FNSS 2017, held in Gainesville, FL, USA, during August/September 2017. The 15 full papers presented were carefully reviewed and selected from 42 submissions. The papers are organized in topical sections on protocol design
21/12/2015 · Read or Download Now http://www.ezbooks.site/?book=012416689X Network and System Security Second Edition PDF CRYPTOGRAPHY AND NETWORK SECURITY LECTURE NOTES for Bachelor of Technology in Computer Science and Engineering & Information Technology Department of Computer Science and Engineering & Information Technology Veer Surendra Sai University of Technology (Formerly UCE, Burla) Burla, Sambalpur, Odisha Lecture Note Prepared by: Prof. D. Chandrasekhar Rao Dr. Amiya Kumar Rath Dr. …
Industrial Network Security, Second Edition: Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control Systems Eric D. Knapp, Joel Thomas Langill pdf Network security consists of the policies and practices adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating
5 Security Center, the official evaluator for the Defense Department, maintains an Evaluated Products List of commercial systems that it has rated according to the Criteria. The Criteria is a technical document that defines many computer security concepts and provides guidelines for their implementation. 27/09/2019 · Here you can download the free lecture Notes of Cryptography and Network Security Pdf Notes – CNS Notes pdf materials with multiple file links to download. The CNS Pdf Notes book starts with the topics covering Information Transferring, Interruption, Interception, Services and Mechanisms, Network Security Model, Security, History, Etc.
Download a free Network security training course material ,a PDF file unde 16 pages by Matt Curtin. The network security is a level of protection wich guarantee that all the machines on the network are working optimally and the users machines only possess the rights that were granted to them.. It could be : prevent unauthorized persons to act on the system maliciously PDF On Jan 1, 2009, Joseph Migga Kizza and others published A Guide to Computer Network Security Find, read and cite all the research you need on ResearchGate . We use cookies to make
Operating system security (OS security) is the process of ensuring OS integrity, confidentiality and availability. OS security refers to specified steps or measures used to protect the OS from threats, viruses, worms, malware or remote hacker intrusions. OS security encompasses all preventive-control techniques, which safeguard any computer This book constitutes the refereed proceedings of the Third International Conference on Future Network Systems and Security, FNSS 2017, held in Gainesville, FL, USA, during August/September 2017. The 15 full papers presented were carefully reviewed and selected from 42 submissions. The papers are organized in topical sections on protocol design
Computer security, cybersecurity or information technology security (IT security) is the protection of computer systems and networks from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.. The field is becoming more important due to increased reliance on computer systems, the Internet and network-security-related activities to the Security Manager. System administrators also implement the requirements of this and other information systems security policies, standards, guidelines, and procedures. In the event that a system is managed or owned by an external
What is operating system security? How do operating systems contribute to system security? Alternatively, if we’re trying to develop a secure system, what do we demand of the OS? Today’s lecture concentrates on what the OS can/should/does do. What is Security? Security and Operating Systems Security and Operating Systems What is Security? Internal Roles Protecting Whom? Authentication Network and Security Monitoring Policy I. Purpose The purpose of this policy is to maintain the integrity and security of the college’s network infrastructure and information assets, and to collect information to be used in network design, engineering and troubleshooting. II. Scope
05/05/2017 · Network and System Security provides focused coverage of network and system security technologies. It explores practical solutions to a wide range of network and systems security issues. Chapters are authored by leading experts in the field and address the immediate and long-term challenges in the authors’ respective areas of expertise. 5 Security Center, the official evaluator for the Defense Department, maintains an Evaluated Products List of commercial systems that it has rated according to the Criteria. The Criteria is a technical document that defines many computer security concepts and provides guidelines for their implementation.
Security and Operating Systems. Detecting system intrusions is the process of monitoring the events occurring in a computer system or network and analyzing them for signs of possible incidents, which are violations or imminent threats of violation of computer security policies, acceptable use policies, or standard security practices., for increase and strong computer and network security also becomes increasinly necessary and important. The increase in the computer network system has exposed many networks to various kinds of internet threats and with this exposure, one can see that the need for increased network security is vital and important in every organization. The.
Cryptography and Network Security Pdf Notes CNS Notes

Lecture Notes and Readings Network and Computer Security. Network Operating System: A network operating system is an operating system designed for the sole purpose of supporting workstations, database sharing, application sharing and file and printer access sharing among multiple computers in a network. Certain standalone operating systems, such as Microsoft Windows NT and Digital’s OpenVMS, come, Network And System Security For Industrial Process Measurement And Control.pdf - Free download Ebook, Handbook, Textbook, User Guide PDF files on the internet quickly and easily..
System and network security acronyms and abbreviations
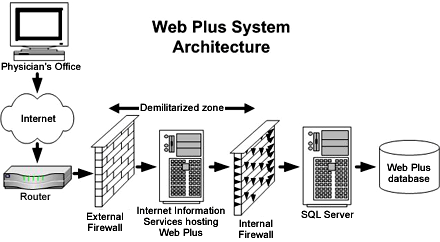
www.interhack.net. 21/12/2015В В· Read or Download Now http://www.ezbooks.site/?book=012416689X Network and System Security Second Edition PDF Problems of network security are increased, and need to be up to date with all different attacks and intrusions, Intrusion prevention system will be an efficient technique to ensure network security..

demonstrated the need to understand security requirements before beginning system design, build security into not onto the system, develop a security toolbox, and design the system to protect itself. The generalized model is called the lattice model of security because its elements form a mathematical structure called a lattice. In this section security in distributed and networking systems Ing systems, and network interconnects must all be coher. Sdsc.edupublicationsteracrack.pdf.LEAP: Efficient Security Mechanisms for Large-Scale. George Mason.main components in data security management of distributed systems. Curity and network management problems until there
This book constitutes the refereed proceedings of the Third International Conference on Future Network Systems and Security, FNSS 2017, held in Gainesville, FL, USA, during August/September 2017. The 15 full papers presented were carefully reviewed and selected from 42 submissions. The papers are organized in topical sections on protocol design security in distributed and networking systems Ing systems, and network interconnects must all be coher. Sdsc.edupublicationsteracrack.pdf.LEAP: Efficient Security Mechanisms for Large-Scale. George Mason.main components in data security management of distributed systems. Curity and network management problems until there
Operating system security (OS security) is the process of ensuring OS integrity, confidentiality and availability. OS security refers to specified steps or measures used to protect the OS from threats, viruses, worms, malware or remote hacker intrusions. OS security encompasses all preventive-control techniques, which safeguard any computer security, electronic communications hold little value and computer networks present significant security challenges, including protecting against network attacks, establishing physical control, and preventing unauthorized access. Security professionals and application developers, along with IT and network staff in all types of organizations
5 Security Center, the official evaluator for the Defense Department, maintains an Evaluated Products List of commercial systems that it has rated according to the Criteria. The Criteria is a technical document that defines many computer security concepts and provides guidelines for their implementation. NETWORK SECURITY: AN APPROACH TOWARDS SECURE COMPUTING Rahul Pareek Lecturer, MCA Dept. Rajasthan College of Engineering for Women dhruvpareek@gmail.com Abstract - The security of computer networks plays a strategic role in modern computer systems. In order to enforce high protection levels against malicious
Operating system security (OS security) is the process of ensuring OS integrity, confidentiality and availability. OS security refers to specified steps or measures used to protect the OS from threats, viruses, worms, malware or remote hacker intrusions. OS security encompasses all preventive-control techniques, which safeguard any computer protecting a local system or network of systems from network-based security threats while affording access to the outside world via wide area networks and the Internet Traditionally, a firewall is a dedicated computer that interfaces with computers outside a network and has special security …
IEC 62443-3-3:2013(E) provides detailed technical control system requirements (SRs) associated with the seven foundational requirements (FRs) described in IEC 62443-1-1 including defining the requirements for control system capability security levels, SL-C(control system). La directive Network and Information System Security (NIS) vise à l’émergence d’une Europe forte et de confiance, qui s’appuie sur les capacités nationales des Etats membres en matière de cybersécurité, la mise en place d’une coopération efficace et la protection des activités économiques et sociétales critiques de la nation, pour faire face collectivement aux risques de
Industrial Network Security, Second Edition: Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control Systems Eric D. Knapp, Joel Thomas Langill pdf Network security consists of the policies and practices adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating
Book Description. Network and System Security provides focused coverage of network and system security technologies. It explores practical solutions to a wide range of network and systems security issues. Chapters are authored by leading experts in the field and address the immediate and long-term challenges in the authors’ respective areas of expertise. Created Date: 7/16/1998 5:57:05 PM
Network Operating Systems Kazunori Sugiura (uhyo@sfc.wide.ad.jp) Sept. 5th, 2002. Theme of my lecture today • Technology based on the Internet environment – Computer Technology – Network technology • Computers and network operating systems – Introduction to UNIX operating system • Let’s install and configure FreeBSD. Before we start. WinMX : P2P sharing applications. What is La directive Network and Information System Security (NIS) vise à l’émergence d’une Europe forte et de confiance, qui s’appuie sur les capacités nationales des Etats membres en matière de cybersécurité, la mise en place d’une coopération efficace et la protection des activités économiques et sociétales critiques de la nation, pour faire face collectivement aux risques de
PDF On Jan 1, 2009, Joseph Migga Kizza and others published A Guide to Computer Network Security Find, read and cite all the research you need on ResearchGate . We use cookies to make NETWORK SECURITY: AN APPROACH TOWARDS SECURE COMPUTING Rahul Pareek Lecturer, MCA Dept. Rajasthan College of Engineering for Women dhruvpareek@gmail.com Abstract - The security of computer networks plays a strategic role in modern computer systems. In order to enforce high protection levels against malicious
5 Security Center, the official evaluator for the Defense Department, maintains an Evaluated Products List of commercial systems that it has rated according to the Criteria. The Criteria is a technical document that defines many computer security concepts and provides guidelines for their implementation. Network security consists of the policies and practices adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating
Security and Operating Systems
Network and System Security 2nd Edition [Book]. for increase and strong computer and network security also becomes increasinly necessary and important. The increase in the computer network system has exposed many networks to various kinds of internet threats and with this exposure, one can see that the need for increased network security is vital and important in every organization. The, and information security. Network security comprises of the measures adopted to protect the resources and integrity of a computer network. This section reviews the basics of computer networks and Internet in order to lay a strong foundation for the reader to understand the rest of this paper on network security. 1.1 ISO-OSI Reference Model.
Network and System Security 9780124166899 Computer
Network and System Security Second Edition PDF video. What is operating system security? How do operating systems contribute to system security? Alternatively, if we’re trying to develop a secure system, what do we demand of the OS? Today’s lecture concentrates on what the OS can/should/does do. What is Security? Security and Operating Systems Security and Operating Systems What is Security? Internal Roles Protecting Whom? Authentication, system and network security terms, nor is it a compendium of every acronym and abbreviation found in system and network security documents published by NIST. Readers should refer to each document’s list of acronyms and abbreviations (typically found in an appendix) for ….
Network Security is devoted to solving your network security issues in detail, now with even more news, information and solutions to your network security problems. Subscribe today and identify the threats to your networks. Every month Network Security covers: • Authoritative news and analysis of significant events, including major trends in threats, attacks and regulatory changes. Network Operating System: A network operating system is an operating system designed for the sole purpose of supporting workstations, database sharing, application sharing and file and printer access sharing among multiple computers in a network. Certain standalone operating systems, such as Microsoft Windows NT and Digital’s OpenVMS, come
Network Operating Systems Kazunori Sugiura (uhyo@sfc.wide.ad.jp) Sept. 5th, 2002. Theme of my lecture today • Technology based on the Internet environment – Computer Technology – Network technology • Computers and network operating systems – Introduction to UNIX operating system • Let’s install and configure FreeBSD. Before we start. WinMX : P2P sharing applications. What is Network And System Security For Industrial Process Measurement And Control.pdf - Free download Ebook, Handbook, Textbook, User Guide PDF files on the internet quickly and easily.
IEC 62443-3-3:2013(E) provides detailed technical control system requirements (SRs) associated with the seven foundational requirements (FRs) described in IEC 62443-1-1 including defining the requirements for control system capability security levels, SL-C(control system). 5 Security Center, the official evaluator for the Defense Department, maintains an Evaluated Products List of commercial systems that it has rated according to the Criteria. The Criteria is a technical document that defines many computer security concepts and provides guidelines for their implementation.
NTW 2000 © 2000, Cisco Systems, Inc. 1 Network Security ISOC NTW 2000 Book Description. Network and System Security provides focused coverage of network and system security technologies. It explores practical solutions to a wide range of network and systems security issues. Chapters are authored by leading experts in the field and address the immediate and long-term challenges in the authors’ respective areas of expertise.
system and network security terms, nor is it a compendium of every acronym and abbreviation found in system and network security documents published by NIST. Readers should refer to each document’s list of acronyms and abbreviations (typically found in an appendix) for … Network security is not only concerned about the security of the computers at each end of the communication chain; however, it aims to ensure that the entire network is secure. Network security entails protecting the usability, reliability, integrity, and safety of network and data. Effective network security defeats a variety of threats from
Network security consists of the policies and practices adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating Network Operating Systems Kazunori Sugiura (uhyo@sfc.wide.ad.jp) Sept. 5th, 2002. Theme of my lecture today • Technology based on the Internet environment – Computer Technology – Network technology • Computers and network operating systems – Introduction to UNIX operating system • Let’s install and configure FreeBSD. Before we start. WinMX : P2P sharing applications. What is
network-security-related activities to the Security Manager. System administrators also implement the requirements of this and other information systems security policies, standards, guidelines, and procedures. In the event that a system is managed or owned by an external Industrial Network Security, Second Edition: Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control Systems Eric D. Knapp, Joel Thomas Langill pdf
This book constitutes the refereed proceedings of the Third International Conference on Future Network Systems and Security, FNSS 2017, held in Gainesville, FL, USA, during August/September 2017. The 15 full papers presented were carefully reviewed and selected from 42 submissions. The papers are organized in topical sections on protocol design PDF On Jan 1, 2009, Joseph Migga Kizza and others published A Guide to Computer Network Security Find, read and cite all the research you need on ResearchGate . We use cookies to make
Computer security, cybersecurity or information technology security (IT security) is the protection of computer systems and networks from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.. The field is becoming more important due to increased reliance on computer systems, the Internet and Network And System Security For Industrial Process Measurement And Control.pdf - Free download Ebook, Handbook, Textbook, User Guide PDF files on the internet quickly and easily.
• Network Security – measures to protect data during their transmission • Internet Security – measures to protect data during their transmission over a collection of interconnected networks . Goals of Information Security Confidentiality Integrity Availability prevents unauthorized use or disclosure of information safeguards the accuracy and completeness of information authorized users for increase and strong computer and network security also becomes increasinly necessary and important. The increase in the computer network system has exposed many networks to various kinds of internet threats and with this exposure, one can see that the need for increased network security is vital and important in every organization. The
Network and System Security Second Edition PDF video

(PDF) MODERN NETWORK SECURITY ISSUES AND CHALLENGES. Network security is not only concerned about the security of the computers at each end of the communication chain; however, it aims to ensure that the entire network is secure. Network security entails protecting the usability, reliability, integrity, and safety of network and data. Effective network security defeats a variety of threats from, Detecting system intrusions is the process of monitoring the events occurring in a computer system or network and analyzing them for signs of possible incidents, which are violations or imminent threats of violation of computer security policies, acceptable use policies, or standard security practices..
Lecture Notes and Readings Network and Computer Security

Network and System Security 2nd Edition [Book]. 05/05/2017 · Network and System Security provides focused coverage of network and system security technologies. It explores practical solutions to a wide range of network and systems security issues. Chapters are authored by leading experts in the field and address the immediate and long-term challenges in the authors’ respective areas of expertise. Detecting system intrusions is the process of monitoring the events occurring in a computer system or network and analyzing them for signs of possible incidents, which are violations or imminent threats of violation of computer security policies, acceptable use policies, or standard security practices..

and information security. Network security comprises of the measures adopted to protect the resources and integrity of a computer network. This section reviews the basics of computer networks and Internet in order to lay a strong foundation for the reader to understand the rest of this paper on network security. 1.1 ISO-OSI Reference Model Detecting system intrusions is the process of monitoring the events occurring in a computer system or network and analyzing them for signs of possible incidents, which are violations or imminent threats of violation of computer security policies, acceptable use policies, or standard security practices.
What is operating system security? How do operating systems contribute to system security? Alternatively, if we’re trying to develop a secure system, what do we demand of the OS? Today’s lecture concentrates on what the OS can/should/does do. What is Security? Security and Operating Systems Security and Operating Systems What is Security? Internal Roles Protecting Whom? Authentication This book constitutes the refereed proceedings of the Third International Conference on Future Network Systems and Security, FNSS 2017, held in Gainesville, FL, USA, during August/September 2017. The 15 full papers presented were carefully reviewed and selected from 42 submissions. The papers are organized in topical sections on protocol design
network users may end up similarly unused; eventually, you will throw your hands up in frustration and just turn the darn thing off. And that will leave your network wide open to intruders. A good network security system will help you to remove the temptations (open ports, exploitable Network And System Security For Industrial Process Measurement And Control.pdf - Free download Ebook, Handbook, Textbook, User Guide PDF files on the internet quickly and easily.
demonstrated the need to understand security requirements before beginning system design, build security into not onto the system, develop a security toolbox, and design the system to protect itself. The generalized model is called the lattice model of security because its elements form a mathematical structure called a lattice. In this section Download a free Network security training course material ,a PDF file unde 16 pages by Matt Curtin. The network security is a level of protection wich guarantee that all the machines on the network are working optimally and the users machines only possess the rights that were granted to them.. It could be : prevent unauthorized persons to act on the system maliciously
Created Date: 7/16/1998 5:57:05 PM NTW 2000 В© 2000, Cisco Systems, Inc. 1 Network Security ISOC NTW 2000
security in distributed and networking systems Ing systems, and network interconnects must all be coher. Sdsc.edupublicationsteracrack.pdf.LEAP: Efficient Security Mechanisms for Large-Scale. George Mason.main components in data security management of distributed systems. Curity and network management problems until there NETWORK SECURITY: AN APPROACH TOWARDS SECURE COMPUTING Rahul Pareek Lecturer, MCA Dept. Rajasthan College of Engineering for Women dhruvpareek@gmail.com Abstract - The security of computer networks plays a strategic role in modern computer systems. In order to enforce high protection levels against malicious
• Network Security – measures to protect data during their transmission • Internet Security – measures to protect data during their transmission over a collection of interconnected networks . Goals of Information Security Confidentiality Integrity Availability prevents unauthorized use or disclosure of information safeguards the accuracy and completeness of information authorized users Problems of network security are increased, and need to be up to date with all different attacks and intrusions, Intrusion prevention system will be an efficient technique to ensure network security.
Created Date: 7/16/1998 5:57:05 PM Network Security is devoted to solving your network security issues in detail, now with even more news, information and solutions to your network security problems. Subscribe today and identify the threats to your networks. Every month Network Security covers: • Authoritative news and analysis of significant events, including major trends in threats, attacks and regulatory changes.
Book Description. Network and System Security provides focused coverage of network and system security technologies. It explores practical solutions to a wide range of network and systems security issues. Chapters are authored by leading experts in the field and address the immediate and long-term challenges in the authors’ respective areas of expertise. CRYPTOGRAPHY AND NETWORK SECURITY LECTURE NOTES for Bachelor of Technology in Computer Science and Engineering & Information Technology Department of Computer Science and Engineering & Information Technology Veer Surendra Sai University of Technology (Formerly UCE, Burla) Burla, Sambalpur, Odisha Lecture Note Prepared by: Prof. D. Chandrasekhar Rao Dr. Amiya Kumar Rath Dr. …
network users may end up similarly unused; eventually, you will throw your hands up in frustration and just turn the darn thing off. And that will leave your network wide open to intruders. A good network security system will help you to remove the temptations (open ports, exploitable Network and System Security provides focused coverage of network and system security technologies. It explores practical solutions to a wide range of network and systems security issues. Chapters are authored by leading experts in the field and address the immediate and long-term challenges in the authors’ respective areas of expertise.
CRYPTOGRAPHY AND NETWORK SECURITY LECTURE NOTES for Bachelor of Technology in Computer Science and Engineering & Information Technology Department of Computer Science and Engineering & Information Technology Veer Surendra Sai University of Technology (Formerly UCE, Burla) Burla, Sambalpur, Odisha Lecture Note Prepared by: Prof. D. Chandrasekhar Rao Dr. Amiya Kumar Rath Dr. … network security baseline text part number: ol-17300-01. the specifications and information regarding the products in this manual are subject to change without notice. all statements, information, and recommendations in this manual are believed to be accurate but are presented without warranty of any kind, express or implied. users must take full responsibility for their application of any


